Open ldap – OpenLDAP is a powerful and versatile open-source directory service that plays a crucial role in modern IT infrastructure. It provides a centralized repository for managing user identities, network resources, and other critical data, enabling efficient and secure access control.
OpenLDAP has a rich history, evolving from its roots in the University of Michigan’s LDAP project to become a widely adopted standard for directory services. It offers a robust set of features, including authentication, authorization, data management, and integration with various applications, making it a valuable tool for organizations of all sizes.
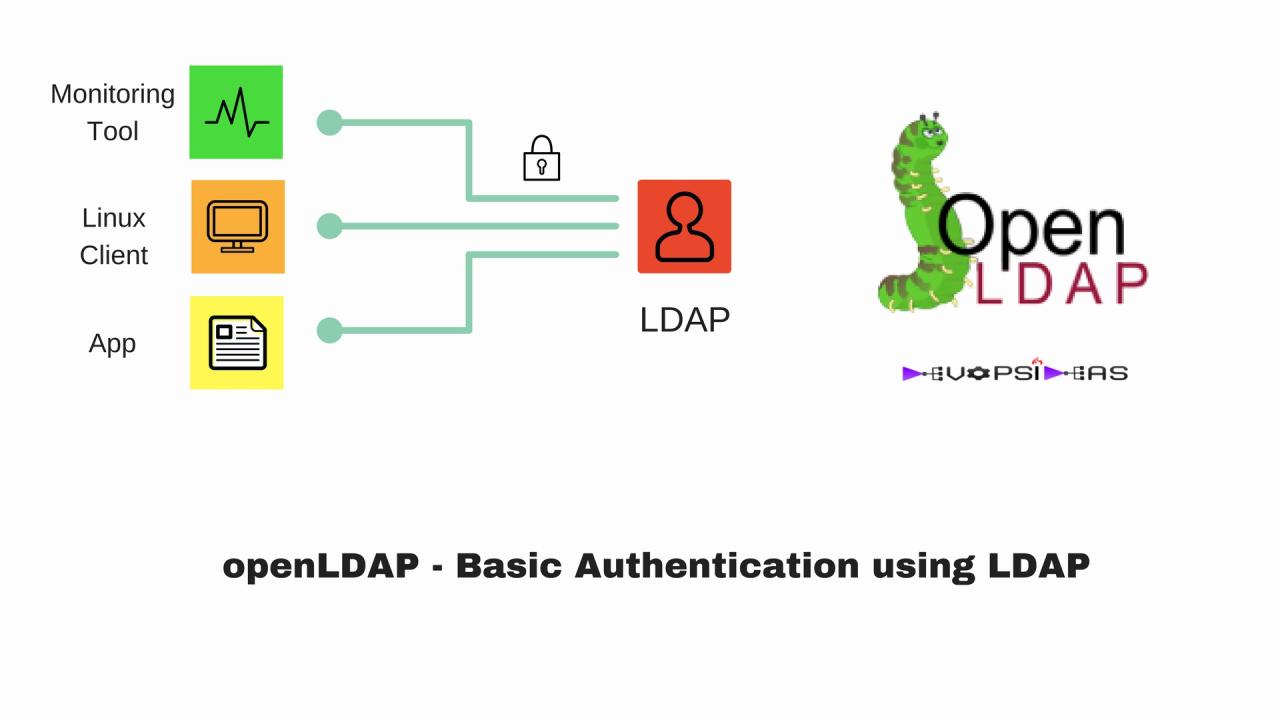
Introduction to OpenLDAP
OpenLDAP is a free and open-source implementation of the Lightweight Directory Access Protocol (LDAP). It provides a robust and scalable directory service, enabling organizations to manage and access user, network, and other critical information effectively. OpenLDAP is a foundational component of many modern IT systems, offering a flexible and extensible solution for directory services.
History and Evolution of OpenLDAP
OpenLDAP originated from the University of Michigan in 1998. It was initially developed as a free and open-source alternative to proprietary directory services, such as Novell’s eDirectory. Since its inception, OpenLDAP has undergone significant development, incorporating new features and enhancements to meet evolving directory service needs. It has become a widely adopted and trusted directory service, used by numerous organizations worldwide.
Core Principles and Design Goals of OpenLDAP
OpenLDAP is built upon several core principles that guide its design and functionality. These principles ensure that OpenLDAP is reliable, secure, and flexible, making it a suitable choice for various directory service applications.
- Open Source and Community Driven: OpenLDAP is developed under the open-source model, allowing for collaborative development and community contributions. This collaborative approach fosters innovation and ensures that OpenLDAP remains relevant and adaptable to evolving industry needs.
- Standards Compliance: OpenLDAP adheres to the LDAP standards, ensuring interoperability with other LDAP-compliant directory services and applications. This adherence to standards simplifies integration and allows for seamless communication between different systems.
- Scalability and Performance: OpenLDAP is designed to handle large directory databases and high volumes of requests. Its scalable architecture enables it to meet the demands of diverse organizations, from small businesses to large enterprises.
- Security and Integrity: OpenLDAP incorporates robust security features to protect sensitive information stored within the directory. It supports various authentication mechanisms, access control mechanisms, and encryption protocols, ensuring data confidentiality and integrity.
- Flexibility and Extensibility: OpenLDAP offers a flexible and extensible architecture that allows for customization and integration with other systems. It supports various data types, schema definitions, and plugins, enabling organizations to tailor OpenLDAP to their specific requirements.
Key Features and Concepts
OpenLDAP is a powerful and versatile directory service that provides a robust foundation for managing user identities, access control, and data in a centralized and secure manner. This section delves into the core features and key concepts of OpenLDAP, providing a comprehensive understanding of its capabilities.
Directory Services
OpenLDAP acts as a central repository for storing and managing information about users, computers, groups, and other resources within an organization. This information is organized in a hierarchical structure, making it easy to retrieve and manage data efficiently.
- User Management: OpenLDAP facilitates the creation, modification, and deletion of user accounts, including setting passwords, assigning roles, and managing user attributes.
- Group Management: It allows the creation and management of groups, enabling the assignment of users to specific groups based on their roles and permissions.
- Resource Management: OpenLDAP can manage information about various resources, such as printers, servers, and network devices, providing a centralized location for managing these assets.
Authentication and Authorization
OpenLDAP plays a crucial role in authenticating users and authorizing their access to resources.
- Authentication: OpenLDAP verifies the identity of users by comparing their credentials (username and password) against the stored information in the directory.
- Authorization: Based on the user’s identity and group memberships, OpenLDAP determines the level of access granted to specific resources.
Data Management
OpenLDAP offers a robust mechanism for storing and managing data in a structured format.
- LDAP Schema: The LDAP schema defines the structure and organization of the data stored in the directory. It specifies the attributes and object classes used to represent different types of information.
- Directory Tree: The directory tree is a hierarchical representation of the data, organized into branches and leaves. Each branch represents a specific category, while the leaves represent individual objects.
- Object Classes: Object classes define the attributes and relationships that characterize different types of objects in the directory. For instance, the “inetOrgPerson” object class represents a person with an internet-related organizational affiliation.
Examples of OpenLDAP Applications
OpenLDAP is widely used in various applications, including:
- Single Sign-On (SSO): OpenLDAP can be integrated with web applications to provide a centralized authentication system, allowing users to log in once and access multiple applications without re-entering their credentials.
- Network Access Control (NAC): OpenLDAP can be used to enforce access control policies for network devices, ensuring that only authorized users and devices can connect to the network.
- Email and Collaboration: OpenLDAP is often used to manage user accounts and access permissions for email servers and collaboration platforms.
- Virtualization and Cloud Computing: OpenLDAP is used to manage user identities and access control in virtualized environments and cloud platforms.
Installation and Configuration
Installing and configuring OpenLDAP involves setting up the necessary software packages and defining the directory structure, schema, and access controls. This process ensures the proper functioning of the directory service and secures sensitive data.
Installation on Different Operating Systems
Installing OpenLDAP on different operating systems is a straightforward process. The specific steps may vary depending on the chosen operating system.
- Ubuntu/Debian: Use the package manager to install OpenLDAP.
sudo apt-get install slapd ldap-utils - Red Hat/CentOS: Install OpenLDAP using the yum package manager.
sudo yum install openldap-servers openldap-clients - macOS: Install OpenLDAP using Homebrew.
brew install openldap - Windows: Download and install OpenLDAP for Windows from the official website. The installation process is guided by a wizard.
Configuration of OpenLDAP
OpenLDAP configuration involves defining the schema, database, and access controls. This ensures that the directory service functions correctly and securely.
Setting Up the Schema
The schema defines the structure and attributes of objects within the directory. The schema is typically stored in the /etc/openldap/schema directory.
- Default Schema: OpenLDAP comes with a default schema that defines common object classes and attributes. This schema can be modified or extended to meet specific requirements.
- Custom Schema: To add custom attributes or object classes, create a new schema file and include it in the
/etc/openldap/schemadirectory. The schema file should define the attributes and object classes in a specific format.
# Example custom schema file
objectClass: myCustomObject
(
top STRUCTURAL
...
)
attributeTypes: myCustomAttribute
(
...
)
- Schema Loading: After creating or modifying the schema, it needs to be loaded into the OpenLDAP server. This is typically done by modifying the
slapd.confconfiguration file.
schema "cn=config" "cn=schema" "myCustomSchema.ldif"
Database Configuration
The OpenLDAP database stores the directory information. The database is typically stored in the /var/lib/ldap directory.
- Database Type: OpenLDAP supports various database types, including Berkeley DB and LDIF. The default database type is Berkeley DB, which provides efficient data storage and retrieval.
- Database Location: The location of the database can be specified in the
slapd.confconfiguration file.
database bdb
suffix "dc=example,dc=com"
directory "/var/lib/ldap"
Access Control
Access controls define which users or groups have access to specific parts of the directory. Access controls are defined in the slapd.conf configuration file using Access Control Lists (ACLs).
- ACLs: ACLs specify the permissions granted to users or groups. Permissions can include read, write, and delete access to specific objects or attributes.
- Example ACL:
access to attrs=*,by=dn="cn=admin,dc=example,dc=com",read,write,delete
access to attrs=*,by=dn="cn=user,dc=example,dc=com",read,write
This ACL grants read, write, and delete access to all attributes for the user with the DN “cn=admin,dc=example,dc=com”, and read and write access to all attributes for the user with the DN “cn=user,dc=example,dc=com”.
Securing OpenLDAP Deployments
Securing OpenLDAP deployments is essential to protect sensitive data. Best practices for securing OpenLDAP include:
- Strong Passwords: Use strong passwords for the administrator account and other users. Strong passwords should be at least 12 characters long and include a mix of uppercase and lowercase letters, numbers, and symbols.
- TLS/SSL Encryption: Enable TLS/SSL encryption to secure communication between clients and the OpenLDAP server. This ensures that data is transmitted securely over the network.
- Access Control Restrictions: Implement strict access control restrictions to limit access to sensitive data. Only authorized users should have access to specific parts of the directory.
- Regular Security Audits: Perform regular security audits to identify and address potential vulnerabilities. This includes reviewing access control lists, checking for outdated software, and monitoring for suspicious activity.
LDAP Clients and Tools
Interacting with OpenLDAP requires specialized clients and tools designed to manage and query directory data. These tools offer various functionalities, from simple browsing to complex scripting and administration tasks.
LDAP Clients
LDAP clients provide a user interface for interacting with OpenLDAP servers. They enable users to browse, search, modify, and delete directory data.
- LDAP Browser: This is a basic client that allows users to browse the directory tree and view entries. It provides a simple graphical interface for navigating and searching directory data. Common examples include:
- Apache Directory Studio: A popular and feature-rich client that offers a comprehensive set of tools for managing LDAP directories. It provides functionalities for browsing, searching, modifying, and deleting entries, as well as for managing schema and replication.
- JNDI (Java Naming and Directory Interface): A Java API that allows Java applications to interact with LDAP directories. It provides a standardized interface for accessing and manipulating directory data, regardless of the underlying LDAP implementation.
- Command-line Tools: Command-line tools offer a more direct and powerful way to interact with OpenLDAP. They provide flexibility and scripting capabilities for automating tasks.
- ldapsearch: This is a fundamental command-line tool for searching and retrieving data from an LDAP server. It allows users to define complex search filters and retrieve specific attributes from entries.
- ldapadd: This tool adds new entries to the directory. It requires specifying the entry’s DN (Distinguished Name), attributes, and values.
- ldapmodify: This tool modifies existing entries in the directory. It allows users to update attribute values or add/remove attributes.
- ldapdelete: This tool removes entries from the directory. It requires specifying the DN of the entry to be deleted.
LDAP Administration Tools, Open ldap
LDAP administration tools are specialized clients designed for managing and configuring OpenLDAP servers. They provide features for managing users, groups, and other directory objects, as well as for configuring server settings and security policies.
- OpenLDAP Administrator’s Guide: The official OpenLDAP documentation provides comprehensive guidance on managing and configuring OpenLDAP servers. It covers topics such as server configuration, schema management, replication, and security.
- SLAPD (Simple LDAP Daemon): This is the core server component of OpenLDAP. It provides the functionality for storing, retrieving, and managing directory data. SLAPD is typically configured through a configuration file (slapd.conf).
- LDAP Utilities: OpenLDAP provides a set of command-line utilities for managing and configuring the server. These utilities include tools for schema management, replication configuration, and access control management.
LDAP Data Management Tools
LDAP data management tools are designed to simplify the management and manipulation of directory data. They provide features for importing, exporting, and transforming data, as well as for managing data consistency and integrity.
- LDAP Import/Export Tools: These tools allow users to import data from external sources, such as CSV files or databases, into an LDAP directory. They also enable exporting data from LDAP into various formats.
- LDAP Data Synchronization Tools: These tools help maintain consistency between multiple LDAP directories or between LDAP and other data sources. They monitor data changes and ensure that updates are replicated across different systems.
LDAP Monitoring and Auditing Tools
LDAP monitoring and auditing tools provide insights into the performance and security of OpenLDAP servers. They allow administrators to track server activity, identify potential issues, and enforce security policies.
- LDAP Performance Monitoring Tools: These tools monitor server performance metrics, such as response times, connection rates, and query execution times. They provide insights into server health and identify potential bottlenecks.
- LDAP Security Auditing Tools: These tools track user activities, access attempts, and security events related to the LDAP server. They help identify unauthorized access attempts, security breaches, and other security threats.
LDAP Scripting and Automation Tools
LDAP scripting and automation tools enable users to automate tasks related to managing and querying directory data. They provide a way to perform repetitive tasks efficiently and reliably.
- LDAP Scripting Languages: Various scripting languages, such as Python, Perl, and Ruby, provide libraries and modules for interacting with LDAP directories. These languages allow users to write scripts for automating tasks such as user provisioning, group management, and data synchronization.
- LDAP Automation Frameworks: Frameworks such as Ansible and Puppet provide modules for managing LDAP servers and directory data. These frameworks allow users to define infrastructure configurations and automate tasks such as server installation, configuration, and user management.
Integration with Other Systems
OpenLDAP’s flexibility allows it to seamlessly integrate with various systems, enhancing overall functionality and streamlining workflows. Its ability to connect with databases, web servers, and applications makes it a valuable asset in modern IT environments.
Integration with Databases
OpenLDAP can be integrated with various databases, such as MySQL, PostgreSQL, and Oracle, to store and manage user information. This integration allows for centralized user management and facilitates data synchronization between different systems.
- Data Replication: OpenLDAP can be configured to replicate data from a database to its directory service, ensuring consistent data across multiple systems. This approach is particularly useful for large-scale deployments where data consistency is paramount.
- User Authentication: OpenLDAP can be used to authenticate users against a database, providing a unified authentication mechanism across different applications and systems. This approach simplifies user management and enhances security.
Integration with Web Servers
OpenLDAP can be integrated with web servers like Apache and Nginx to provide authentication and authorization services. This integration enables secure access to web applications and resources, enhancing security and user experience.
- LDAP Authentication: OpenLDAP can be configured to authenticate users against a web server, allowing users to access web applications using their LDAP credentials. This approach eliminates the need for separate user accounts for each application, simplifying user management.
- Authorization Control: OpenLDAP can be used to define access control lists (ACLs) for web resources, allowing administrators to restrict access to specific users or groups. This approach enhances security by limiting access to sensitive information and resources.
Integration with Applications
OpenLDAP can be integrated with various applications, including email servers, CRM systems, and enterprise resource planning (ERP) software, to manage user information and provide authentication services. This integration enhances application functionality and simplifies user management.
- User Provisioning: OpenLDAP can be used to automate user provisioning for applications, automatically creating and updating user accounts based on changes in the LDAP directory. This approach simplifies user management and reduces administrative overhead.
- Group Management: OpenLDAP can be used to manage user groups for applications, allowing administrators to define access permissions based on group membership. This approach provides a centralized mechanism for managing user access to applications and resources.
Single Sign-On (SSO)
OpenLDAP can be used to implement Single Sign-On (SSO), allowing users to authenticate once and access multiple applications and resources without re-entering their credentials. This approach enhances user experience and improves security by reducing the number of passwords users need to manage.
- LDAP-based SSO: OpenLDAP can be used as a central authentication source for SSO solutions, providing a unified authentication mechanism across multiple applications and systems. This approach simplifies user management and enhances security.
- SSO Integration: OpenLDAP can be integrated with SSO solutions like Shibboleth and OpenID Connect, providing a secure and scalable authentication mechanism for web applications and services.
Directory Synchronization
OpenLDAP can be used to synchronize directory data with other systems, ensuring consistent user information across multiple platforms. This approach is essential for organizations that rely on multiple systems for user management and authentication.
- LDAP Synchronization Tools: Several tools, such as Apache Directory Studio and JXplorer, can be used to synchronize directory data between OpenLDAP and other systems, ensuring data consistency and reducing administrative overhead.
- Synchronization Methods: OpenLDAP supports various synchronization methods, including replication, import/export, and delta synchronization, allowing administrators to choose the most appropriate method based on their specific requirements.
Common Use Cases
OpenLDAP, with its flexibility and robust feature set, finds applications across diverse domains. Its capabilities extend beyond directory services, encompassing a wide range of use cases, including IT management, network services, and application development. Understanding these use cases can help you grasp the versatility of OpenLDAP and its potential in your specific environment.
IT Management
OpenLDAP plays a crucial role in managing IT resources and user identities within an organization. It facilitates centralized authentication, authorization, and user management, simplifying administrative tasks and enhancing security.
- User Management: OpenLDAP enables the creation, modification, and deletion of user accounts, including assigning roles, permissions, and access controls. This centralized approach streamlines user administration and ensures consistent policies across the organization.
- Authentication and Authorization: OpenLDAP provides a secure mechanism for authenticating users and granting access to resources based on their permissions. It integrates with various applications and services, enabling single sign-on (SSO) and streamlined access control.
- Group Management: OpenLDAP supports group management, allowing administrators to define groups, assign users to groups, and manage group memberships. This simplifies access control and enables granular permissions based on group affiliation.
Network Services
OpenLDAP is commonly used in network services, facilitating secure and efficient management of network devices and resources.
- Network Device Management: OpenLDAP can be used to manage network devices, such as routers, switches, and firewalls. It allows administrators to configure, monitor, and control these devices centrally, simplifying network administration and ensuring consistency across the infrastructure.
- DNS Integration: OpenLDAP integrates with DNS services, providing a centralized repository for managing DNS records. This simplifies DNS administration and ensures consistency across the network.
- DHCP Integration: OpenLDAP can be used to manage DHCP services, enabling centralized configuration and allocation of IP addresses to network devices. This streamlines DHCP administration and enhances network security.
Application Development
OpenLDAP offers a powerful platform for developing applications that require secure and efficient directory services.
- User Authentication and Authorization: OpenLDAP provides a robust authentication and authorization framework for applications, allowing developers to integrate secure user management into their software.
- Data Storage and Retrieval: OpenLDAP serves as a reliable and scalable data store for applications, enabling efficient storage and retrieval of user information, configuration settings, and other data.
- Integration with Other Systems: OpenLDAP seamlessly integrates with other systems, enabling applications to leverage existing directory services and data sources.
Real-World Examples
OpenLDAP finds applications in various industries, including:
- Education: Universities and schools use OpenLDAP for managing student and faculty accounts, providing access to resources, and maintaining directory services for their campus networks.
- Healthcare: Hospitals and healthcare providers utilize OpenLDAP for managing patient records, staff accounts, and medical device data, ensuring secure and compliant data storage and access.
- Finance: Financial institutions rely on OpenLDAP for managing customer accounts, employee information, and financial transactions, ensuring secure and reliable data management.
Alternatives to OpenLDAP
OpenLDAP, while a robust and widely used directory service, is not the only option available. Various alternatives, both commercial and open-source, offer distinct features and cater to specific needs. Understanding these alternatives allows for informed decision-making based on the requirements of your specific use case.
Comparison with Microsoft Active Directory
Microsoft Active Directory (AD) is a widely adopted directory service, primarily used within Windows environments. Both OpenLDAP and AD provide similar functionalities, such as user and group management, authentication, and authorization. However, they differ in their implementation and target audiences.
Key Differences
- Operating System: AD is tightly integrated with Windows operating systems, while OpenLDAP is platform-independent and runs on various operating systems like Linux, Unix, and macOS.
- Cost: OpenLDAP is open-source and free to use, while AD is a commercial product requiring licensing fees.
- Complexity: AD is known for its complexity, especially in large-scale deployments, while OpenLDAP is considered more lightweight and easier to manage.
- Integration: AD seamlessly integrates with other Microsoft products, while OpenLDAP offers greater flexibility in integrating with various systems through its APIs.
Advantages and Disadvantages
- OpenLDAP:
- Advantages: Open-source, platform-independent, flexible, cost-effective.
- Disadvantages: Requires more technical expertise, limited integration with Windows environments.
- Active Directory:
- Advantages: Tightly integrated with Windows, extensive management tools, comprehensive features.
- Disadvantages: Commercial product, complex, limited platform support, higher cost.
Open-Source Alternatives
Several open-source directory services offer alternatives to OpenLDAP. These alternatives provide similar functionalities but may have unique strengths and weaknesses.
Key Open-Source Alternatives
| Directory Service | Key Features | Target Use Cases |
|---|---|---|
| 389 Directory Server | Highly scalable, supports multiple protocols, integrates with various systems. | Large-scale deployments, enterprise-level directory services. |
| Apache Directory Server | Lightweight, easy to configure, supports multiple protocols, good for small-scale deployments. | Small to medium-sized organizations, development environments, testing. |
| FreeIPA | Comprehensive directory service, includes centralized authentication, authorization, and policy management. | Enterprise-level deployments, Linux-based environments. |
| OpenDJ | Supports multiple protocols, high performance, integrates with Java applications. | Java-based applications, cloud environments, enterprise-level directory services. |
Future of OpenLDAP: Open Ldap
OpenLDAP, a robust and widely adopted directory service, continues to evolve, adapting to the changing demands of modern IT landscapes. While it has proven its worth in traditional enterprise environments, its future lies in embracing emerging trends and leveraging its strengths to address new challenges.
Emerging Trends and Advancements
The future of OpenLDAP is intertwined with the evolution of directory services and the broader IT landscape. Key trends shaping its development include:
- Cloud-Native Architecture: OpenLDAP is increasingly being deployed in cloud environments, leveraging containerization and orchestration technologies like Docker and Kubernetes. This enables scalable, flexible, and resilient directory services that can be easily provisioned and managed in the cloud.
- Microservices and API-Driven Development: OpenLDAP is being integrated with microservices architectures, providing authentication and authorization services through APIs. This allows for greater flexibility and interoperability, enabling seamless integration with various applications and services.
- Security Enhancements: OpenLDAP is continuously evolving to address emerging security threats. Advancements include support for stronger authentication mechanisms, encryption protocols, and access control policies, ensuring the security and integrity of sensitive data.
- Automation and DevOps: OpenLDAP is becoming increasingly automated, leveraging scripting and configuration management tools to streamline deployments, updates, and maintenance. This aligns with DevOps principles, enabling faster and more efficient directory service management.
Potential Future Applications and Use Cases
OpenLDAP’s versatility and adaptability extend beyond traditional directory service roles. Emerging use cases include:
- Internet of Things (IoT) Management: OpenLDAP can be used to manage and authenticate devices in IoT environments, providing a centralized platform for device registration, configuration, and access control.
- Edge Computing: As edge computing gains traction, OpenLDAP can play a crucial role in managing and securing data and services at the edge. This enables distributed directory services that are closer to users and devices, reducing latency and improving performance.
- Identity and Access Management (IAM) for Cloud Applications: OpenLDAP can be used to provide centralized IAM for cloud applications, enabling secure access control and user management across various cloud platforms.
- Blockchain Integration: OpenLDAP can be integrated with blockchain technology to enhance security, immutability, and transparency in directory services. This can be particularly beneficial for managing digital identities and sensitive data.
Predictions About the Future Direction of OpenLDAP
Based on current trends and advancements, OpenLDAP is expected to continue its evolution as a key component of directory services:
- Increased Cloud Adoption: OpenLDAP will see greater adoption in cloud environments, with more cloud-native offerings and integrations with popular cloud platforms.
- Enhanced Security Features: OpenLDAP will continue to strengthen its security features, incorporating advanced authentication mechanisms, encryption protocols, and access control policies to address evolving threats.
- Greater Interoperability: OpenLDAP will focus on improving interoperability with other systems, enabling seamless integration with various applications and services through APIs and open standards.
- Focus on Automation and DevOps: OpenLDAP will further embrace automation and DevOps principles, providing tools and features that simplify deployment, management, and maintenance.
Final Review
OpenLDAP empowers organizations to manage their IT resources effectively and securely. From user authentication and authorization to data management and integration with other systems, OpenLDAP provides a comprehensive solution for directory services. As technology continues to evolve, OpenLDAP remains a cornerstone of modern IT infrastructure, offering a reliable and flexible platform for managing data and access control.
OpenLDAP is a powerful tool for managing user identities and permissions, especially in larger organizations. However, sometimes you need a more creative approach, like crafting your own custom solution. That’s where DIY projects like diy mod podge come in handy.
While not directly related to OpenLDAP, these DIY projects often involve similar principles of resourcefulness and customization, which can be applied to optimizing your OpenLDAP setup.
