Server monitoring is crucial for any WordPress website, ensuring optimal performance and preventing downtime. It provides insights into your server’s health, allowing you to identify and address issues before they impact your visitors. By tracking key metrics like CPU usage, memory consumption, and disk space, you can proactively optimize your site’s resources, leading to a smoother user experience and improved search engine rankings.
Understanding the intricacies of server monitoring empowers you to take control of your website’s performance. Whether you’re a seasoned developer or a casual blogger, a robust monitoring system can be your secret weapon for maintaining a healthy and thriving online presence.
Troubleshooting Server Issues
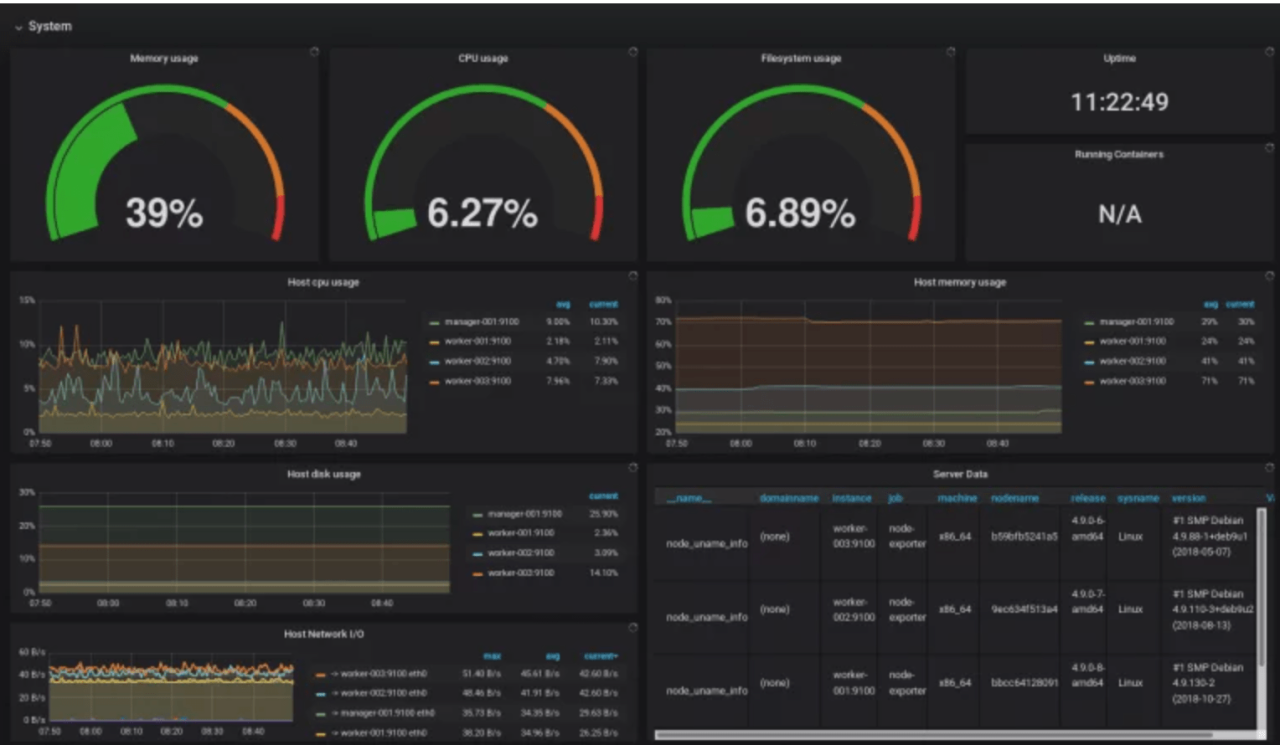
Server monitoring data plays a crucial role in identifying and diagnosing server issues. By analyzing the collected metrics and logs, administrators can pinpoint the root cause of problems and take appropriate corrective actions. This process involves a systematic approach to investigate and resolve server performance degradation, unexpected downtime, or other anomalies.
Analyzing Logs and Metrics
Analyzing logs and metrics is a fundamental step in troubleshooting server issues. Logs provide a detailed record of events, errors, and warnings, while metrics offer real-time insights into server performance. By correlating log entries with corresponding metric spikes or dips, administrators can identify patterns and potential causes of problems. For instance, if a server’s CPU utilization suddenly surges, examining the system logs might reveal a specific process consuming excessive resources. Similarly, a sharp increase in network traffic could be linked to a denial-of-service attack, as indicated by security logs.
Troubleshooting Process
Troubleshooting server issues using monitoring data involves a systematic approach. The following flowchart illustrates the steps involved:
- Identify the Problem: The first step is to identify the problem based on observed symptoms. This could involve reviewing alerts generated by the monitoring system, analyzing dashboards, or receiving user reports.
- Gather Monitoring Data: Once the problem is identified, the next step is to gather relevant monitoring data. This includes collecting metrics like CPU usage, memory utilization, disk I/O, network traffic, and logs related to the affected system.
- Analyze the Data: Analyze the collected data to identify patterns and anomalies. Look for sudden spikes or dips in metrics, error messages in logs, or unusual behavior compared to historical data.
- Isolate the Root Cause: Based on the analysis, isolate the root cause of the problem. This could involve identifying a specific process consuming excessive resources, a faulty hardware component, or a configuration issue.
- Implement a Solution: Once the root cause is identified, implement a solution to resolve the issue. This might involve restarting a service, updating software, adjusting configuration settings, or replacing a faulty hardware component.
- Validate the Solution: After implementing the solution, validate its effectiveness by monitoring the server’s performance and ensuring the problem is resolved. Review metrics and logs to confirm the issue is no longer present.
- Document the Issue: Finally, document the issue and the solution implemented for future reference. This helps maintain a record of past incidents and facilitates faster troubleshooting in the future.
Security Monitoring
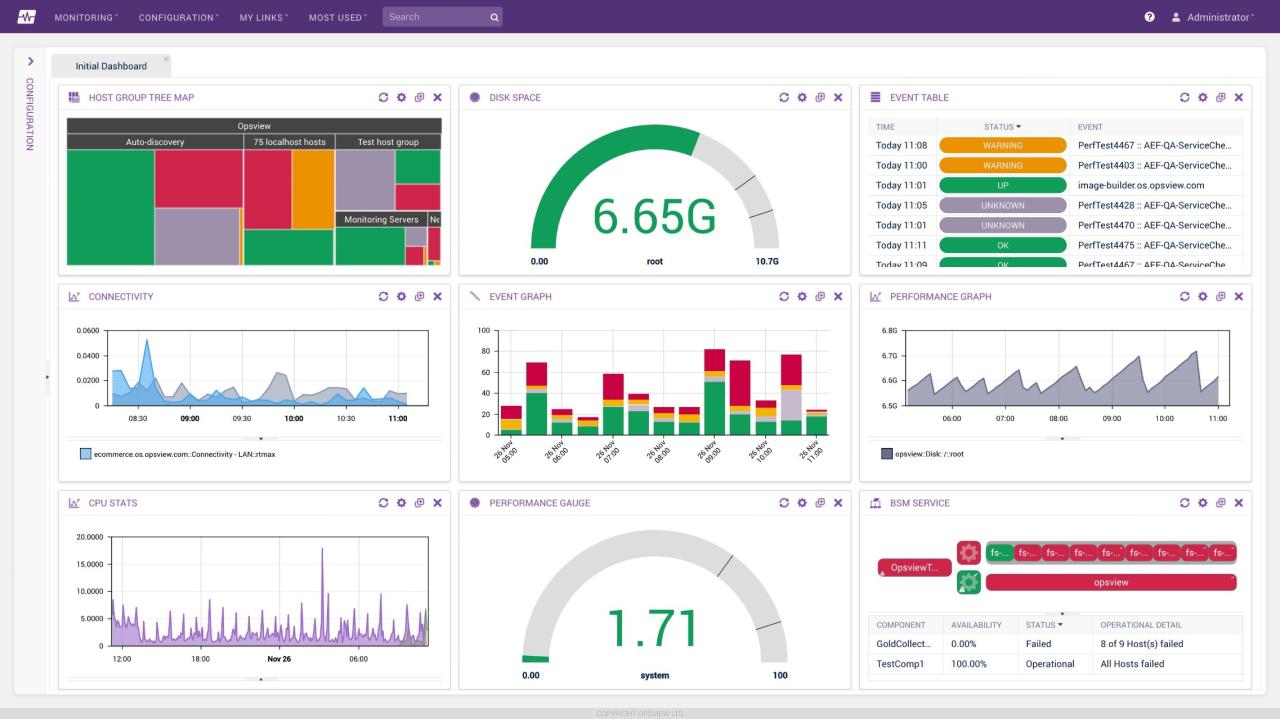
In the ever-evolving landscape of cyber threats, safeguarding your servers is paramount. Proactive security monitoring plays a crucial role in detecting and preventing potential breaches, ensuring the integrity and confidentiality of your valuable data.
Key Security Metrics
Tracking key security metrics provides valuable insights into the security posture of your servers. These metrics can help identify potential vulnerabilities, detect suspicious activities, and enable timely responses to security incidents.
- Intrusion Attempts: Monitoring intrusion attempts, such as failed login attempts, unauthorized access attempts, and attempts to exploit known vulnerabilities, helps identify potential threats and malicious actors targeting your servers.
- Malware Activity: Tracking malware activity, such as the presence of known malware signatures, suspicious file downloads, and unusual process behavior, can help detect and mitigate malware infections.
- Unauthorized Access: Monitoring unauthorized access attempts, such as attempts to access restricted areas of the server or access data without proper authorization, helps identify potential security breaches and unauthorized access.
- Network Traffic Analysis: Analyzing network traffic patterns can reveal suspicious activities, such as unusual traffic volumes, connections to known malicious IP addresses, and encrypted traffic that may indicate data exfiltration.
- Log Analysis: Regularly reviewing server logs for suspicious events, such as failed login attempts, unusual system calls, and file access patterns, can provide valuable insights into potential security threats.
Security Monitoring Tools
Security monitoring tools play a vital role in automating the process of tracking security metrics and detecting potential threats. These tools provide real-time insights into server security, enabling timely responses to security incidents.
- Security Information and Event Management (SIEM): SIEM tools collect and analyze security events from various sources, providing a centralized view of security incidents. They can detect anomalies, correlate events, and generate alerts based on predefined rules.
- Intrusion Detection Systems (IDS): IDS tools monitor network traffic for suspicious patterns and activities, detecting potential intrusions and alerting administrators. They can identify known attack signatures, detect network anomalies, and provide real-time intrusion detection capabilities.
- Vulnerability Scanners: Vulnerability scanners automatically scan servers for known vulnerabilities, identifying potential weaknesses that attackers could exploit. They provide a comprehensive assessment of server security and help prioritize remediation efforts.
- Antivirus and Anti-Malware Software: Antivirus and anti-malware software protect servers from known malware threats, detecting and removing malicious files and software. They provide real-time protection against malware attacks and help mitigate the impact of infections.
- Firewall: A firewall acts as a barrier between the server and the external network, blocking unauthorized access attempts and controlling network traffic. It helps protect servers from external threats and ensures only authorized connections are allowed.
Server Monitoring Best Practices
Server monitoring is crucial for ensuring optimal performance, uptime, and security of your systems. Implementing best practices can help you identify and address potential issues proactively, minimizing downtime and maximizing efficiency.
Establishing Clear Monitoring Goals and Objectives
Before implementing any monitoring solution, it’s essential to define clear goals and objectives. These should align with your overall business needs and priorities.
- Identify Key Performance Indicators (KPIs): Define the metrics that are most important for your business, such as server uptime, response time, resource utilization, and error rates.
- Set Thresholds and Alerts: Determine acceptable performance levels for your KPIs and configure alerts to notify you when these thresholds are exceeded. This ensures you’re alerted to potential issues promptly.
- Define Reporting Requirements: Establish the frequency and format of reports you need to analyze server performance data. This helps you identify trends, track progress, and make informed decisions.
Creating a Comprehensive Monitoring Strategy, Server monitoring
A comprehensive monitoring strategy encompasses various aspects of your server infrastructure.
- System Monitoring: Monitor essential system components like CPU, memory, disk space, and network traffic to ensure they operate within acceptable limits.
- Application Monitoring: Track the performance of your applications, including response time, error rates, and user activity.
- Log Monitoring: Analyze system and application logs to identify potential issues, security threats, and user behavior patterns.
- Security Monitoring: Monitor for suspicious activity, security vulnerabilities, and unauthorized access attempts.
- Network Monitoring: Monitor network performance, bandwidth usage, and latency to identify bottlenecks and connectivity issues.
Choosing the Right Monitoring Tools
The market offers a wide range of monitoring tools, each with its strengths and weaknesses.
- Consider Your Needs: Evaluate your specific monitoring requirements, budget, and technical expertise to choose a tool that best suits your needs.
- Features and Functionality: Look for tools that provide comprehensive monitoring capabilities, including real-time dashboards, alerts, reporting, and integrations with other systems.
- Ease of Use and Scalability: Choose a tool that is easy to configure and use, and can scale as your infrastructure grows.
Implementing Monitoring Solutions
Once you’ve chosen your monitoring tools, it’s crucial to implement them effectively.
- Proper Configuration: Configure your monitoring tools to monitor the relevant metrics and generate alerts when needed.
- Testing and Validation: Thoroughly test your monitoring solution to ensure it’s functioning correctly and providing accurate data.
- Regular Maintenance: Regularly update your monitoring tools, review configurations, and ensure they remain effective over time.
Analyzing and Responding to Alerts
Promptly responding to alerts is essential for mitigating potential issues.
- Prioritize Alerts: Categorize alerts based on their severity and urgency to focus on the most critical issues first.
- Investigate Root Causes: Analyze the data provided by the monitoring tools to identify the root cause of the issue.
- Implement Solutions: Take appropriate action to address the identified issue, whether it’s restarting a service, fixing a configuration error, or addressing a security vulnerability.
Continuous Improvement
Server monitoring is an ongoing process that requires continuous improvement.
- Regularly Review Monitoring Data: Analyze monitoring data to identify trends, patterns, and areas for improvement.
- Optimize Monitoring Configurations: Adjust your monitoring configurations based on your findings and evolving needs.
- Stay Updated on Best Practices: Stay informed about the latest server monitoring best practices and tools to ensure your strategy remains effective.
Final Thoughts
Implementing a comprehensive server monitoring system is an investment in your WordPress website’s future. By proactively tracking performance, security, and resource utilization, you can ensure a seamless experience for your visitors, avoid costly downtime, and optimize your site’s overall efficiency. With the right tools and strategies, server monitoring becomes an invaluable asset for any WordPress website owner.
Server monitoring is crucial for ensuring optimal performance and preventing downtime. It’s a lot like keeping an eye on your finances, making sure everything is running smoothly. If you’re looking for ways to manage your finances effectively, you might want to check out money lei diy , a resource that provides tips on managing your money.
Similarly, with server monitoring, you can identify potential issues before they become major problems, ensuring your systems stay up and running.
