Web based ssh – Web-based SSH offers a modern and convenient way to access remote servers, eliminating the need for traditional SSH clients. This approach provides a user-friendly interface accessible from any web browser, making it ideal for various scenarios, from managing cloud infrastructure to troubleshooting web applications.
Imagine effortlessly connecting to your servers from anywhere with just a web browser, eliminating the need to download and configure software. This is the power of web-based SSH, simplifying remote access and empowering users with greater flexibility.
Introduction to Web-Based SSH
Web-based SSH provides a secure way to access remote servers and execute commands through a web browser, eliminating the need for traditional SSH clients. This approach leverages the power of SSH, a secure protocol designed for remote access and secure communication, and makes it accessible through a user-friendly web interface.
Advantages of Web-Based SSH
Web-based SSH offers several advantages over traditional SSH clients, making it a compelling option for various scenarios.
- Platform Independence: Web-based SSH eliminates the need to install specific SSH clients on different operating systems, as it can be accessed from any device with a web browser. This makes it highly accessible and convenient for users with diverse computing environments.
- Ease of Use: Web-based SSH provides a simplified user interface, making it easier for users to connect to remote servers and execute commands without needing to navigate complex command-line interfaces. This is particularly beneficial for users who are less familiar with traditional SSH clients.
- Enhanced Security: Web-based SSH often incorporates additional security measures, such as two-factor authentication and secure communication protocols, to protect against unauthorized access and data breaches. This makes it a more secure option for accessing sensitive systems and data.
- Centralized Management: Web-based SSH solutions can be centrally managed, allowing administrators to control user access, configure security settings, and monitor usage patterns. This simplifies administration and ensures consistent security practices across the organization.
Scenarios for Web-Based SSH
Web-based SSH is particularly useful in several scenarios, including:
- Remote Server Management: Web-based SSH provides a convenient way for system administrators to manage remote servers from any location with an internet connection. This eliminates the need to be physically present at the server location, streamlining administrative tasks and improving efficiency.
- DevOps and Cloud Environments: Web-based SSH is widely used in DevOps and cloud environments, where developers and operations teams need to access and manage servers and applications remotely. Its platform independence and ease of use make it a valuable tool for these dynamic environments.
- Secure Access for Remote Workers: Web-based SSH allows remote workers to securely access company servers and resources without needing to install specific software on their personal devices. This ensures secure access while maintaining compliance with company security policies.
Web-Based SSH Clients
Web-based SSH clients offer a convenient and accessible way to manage remote servers without installing dedicated software. These clients run entirely within a web browser, making them ideal for accessing servers from various devices without compromising security.
Popular Web-Based SSH Clients
Web-based SSH clients provide a secure and efficient way to connect to remote servers. Here’s a list of popular web-based SSH clients, highlighting their features and capabilities:
| Client Name | Features | Pros | Cons |
|---|---|---|---|
| Termius Web |
|
|
|
| Mosh |
|
|
|
| Bitvise Tunnelier |
|
|
|
| Webmin |
|
|
|
Security Considerations
While web-based SSH offers convenience, it introduces new security challenges. It’s crucial to understand the potential vulnerabilities and risks associated with this approach and implement appropriate mitigation strategies to ensure secure access.
Vulnerabilities and Risks
Web-based SSH relies on a web server and client to establish a connection. This introduces potential vulnerabilities that can be exploited by attackers to compromise the system. Some common vulnerabilities include:
- Cross-Site Scripting (XSS): Attackers can inject malicious scripts into the web application, which can steal user credentials or execute unauthorized commands.
- Man-in-the-Middle (MITM) Attacks: Attackers can intercept the communication between the client and server, potentially capturing sensitive information like passwords and SSH keys.
- Server-Side Vulnerabilities: Weak configurations or vulnerabilities in the web server software can expose the SSH server to attacks.
- Client-Side Vulnerabilities: Security flaws in the web browser or SSH client can be exploited to compromise the system.
Mitigation Strategies
To mitigate these risks, it’s essential to implement robust security measures:
- Use a Secure Web Server: Deploy a secure web server with strong authentication mechanisms and regularly update the software to patch vulnerabilities.
- Enable HTTPS: Ensure all communication between the client and server is encrypted using HTTPS. This prevents eavesdropping and MITM attacks.
- Implement Strong Authentication: Utilize two-factor authentication (2FA) for both the web server and the SSH server to enhance security.
- Secure the SSH Server: Configure the SSH server with strong passwords, disable password authentication, and use SSH keys for secure access.
- Regular Security Audits: Conduct regular security audits to identify and address any potential vulnerabilities.
- Use a Trusted Web-Based SSH Client: Choose a reputable and well-maintained web-based SSH client that has a strong security track record.
Secure Configurations and Practices, Web based ssh
Here are some recommendations for secure configurations and practices:
- Use a Dedicated Web Server: Avoid running the web server and SSH server on the same machine. This reduces the risk of compromise.
- Limit Access: Restrict access to the web-based SSH service to authorized users and devices.
- Use a Firewall: Implement a firewall to block unauthorized access to the web server and SSH server.
- Regularly Update Software: Keep all software components, including the web server, SSH server, and web-based SSH client, up-to-date with the latest security patches.
- Monitor Logs: Regularly monitor logs for suspicious activity to detect and respond to potential security incidents.
- Implement a Security Information and Event Management (SIEM) System: A SIEM system can help to centralize security logs and provide real-time threat detection and response capabilities.
Implementation and Setup
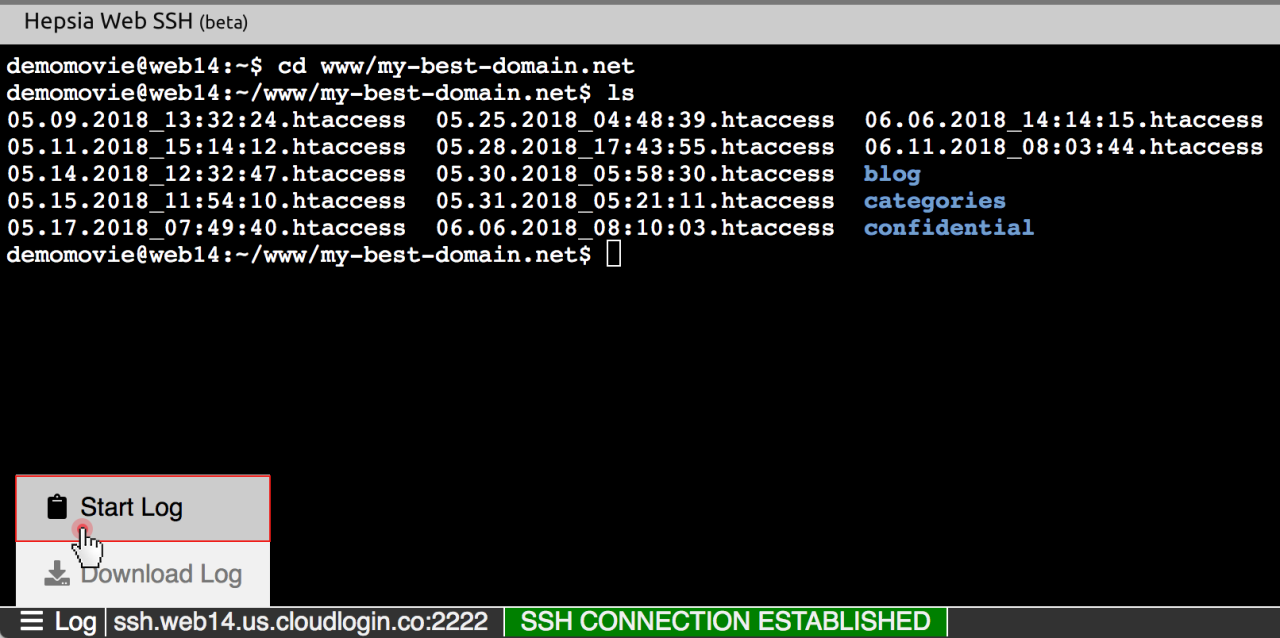
Setting up a web-based SSH server involves several steps, including server configuration, web server setup, and client configuration. This section delves into the details of these steps, providing a comprehensive guide to implementing and configuring a web-based SSH solution.
Web-Based SSH Server Setup
Setting up a web-based SSH server requires configuring both the SSH server and the web server. The SSH server handles the secure connections, while the web server acts as the interface for accessing the SSH service through a web browser.
- SSH Server Configuration: The SSH server needs to be configured to accept connections from the web server. This involves setting up port forwarding rules and configuring the SSH daemon to allow connections from specific IP addresses or networks.
- Web Server Setup: The web server needs to be configured to forward incoming HTTP requests to the SSH server. This can be done using reverse proxy configurations or by setting up a dedicated web server application that handles the communication between the web browser and the SSH server.
Web-Based SSH Client Configuration
Web-based SSH clients are typically web applications that provide a user interface for connecting to SSH servers through a web browser. These clients can be standalone applications or integrated into existing web platforms.
- Client-Side Configuration: Web-based SSH clients may require specific configuration settings to connect to the SSH server. This can include specifying the server address, port number, authentication method, and other connection parameters.
- Client Features: Different web-based SSH clients offer various features, such as terminal emulation, file transfer capabilities, and support for different SSH protocols. The choice of client depends on the specific requirements and preferences of the user.
Code Snippets for Common Configurations
Here are some code snippets for common configurations:
- SSH Server Configuration (OpenSSH):
# Enable port forwarding
PortForwarding yes# Allow connections from a specific IP address
AllowUsers [email protected]# Set the listening port
Port 2222
- Nginx Reverse Proxy Configuration:
location /ssh
proxy_pass http://localhost:2222;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
Closing Summary: Web Based Ssh
As technology evolves, web-based SSH continues to gain popularity, offering a secure and accessible way to manage remote systems. Whether you’re a seasoned developer or a system administrator, web-based SSH provides a powerful and user-friendly tool to streamline your workflow and enhance productivity.
Web-based SSH allows you to securely access remote servers from your browser, which can be especially useful for managing tasks like database administration. For example, you might use SSH to connect to a server running SQL Server 2017 Express to perform database backups or updates.
While SSH is often used for command-line access, there are web-based SSH clients that provide a graphical interface for managing remote servers.